IOC Detection and Response: Strategies for Immediate Threat Containment
.elementor-widget-text-editor.elementor-drop-cap-view-stacked .elementor-drop-cap{background-color:#69727d;color:#fff}.elementor-widget-text-editor.elementor-drop-cap-view-framed .elementor-drop-cap{color:#69727d;border:3px solid;background-color:transparent}.elementor-widget-text-editor:not(.elementor-drop-cap-view-default) .elementor-drop-cap{margin-top:8px}.elementor-widget-text-editor:not(.elementor-drop-cap-view-default) .elementor-drop-cap-letter{width:1em;height:1em}.elementor-widget-text-editor .elementor-drop-cap{float:left;text-align:center;line-height:1;font-size:50px}.elementor-widget-text-editor .elementor-drop-cap-letter{display:inline-block}
Indicators of Compromise (IoCs) act as digital forensic breadcrumbs that point to data breaches. IoCs help identify malicious activity, but traditional detection methods mostly react to incidents after they occur. A compromise likely happens before anyone spots an indicator. Organizations need immediate detection capabilities to minimize damage and contain security threats before they grow.
This piece will share proven strategies for quick threat containment. We’ll get into the challenges of traditional indicators of compromise (IOC) detection methods and show how organizations can build incident response frameworks that cut down detection and containment times.
.elementor-heading-title{padding:0;margin:0;line-height:1}.elementor-widget-heading .elementor-heading-title[class*=elementor-size-]>a{color:inherit;font-size:inherit;line-height:inherit}.elementor-widget-heading .elementor-heading-title.elementor-size-small{font-size:15px}.elementor-widget-heading .elementor-heading-title.elementor-size-medium{font-size:19px}.elementor-widget-heading .elementor-heading-title.elementor-size-large{font-size:29px}.elementor-widget-heading .elementor-heading-title.elementor-size-xl{font-size:39px}.elementor-widget-heading .elementor-heading-title.elementor-size-xxl{font-size:59px}
What are Indicators of Compromise?
Indicators of Compromise (IOCs) serve as forensic breadcrumbs that security professionals use to identify potential security breaches in networks or systems. These digital clues help us track malicious activity and understand cyber-attack patterns during threat hunting.
Common Indicators of Compromise include:
-
Malicious domain names and IP addresses -
Suspicious registry changes -
Suspicious file hashes -
Anomalous network traffic patterns
Monitoring these indicators enables early detection of threats, allowing for swift response and mitigation.
Types of IOCs:
-
File-based IOCs: File hashes, registry key changes, and unauthorized scripts. -
Network-based IOCs: Outbound traffic to command-and-control servers, unusual DNS requests. -
Behavioral IOCs: Unusual login attempts, multiple failed login attempts, spikes in database reads, or remote access request from odd geolocations.
Behavioral indicators of compromise (IOC) offer strong early-warning signs. Unlike static indicators, they’re harder for attackers to disguise, making them essential for real-time detection.
Security teams should also monitor for unexpected HTML response sizes, suspicious processes, and network traffic anomalies from strange geographic regions.
Challenges with Traditional indicators of compromise IOC Detection
Traditional indicators of compromise (IOC) detection methods create major security challenges despite their wide use. Security teams don’t deal very well with basic limitations that slow down threat response. Our team at Fidelis Security has seen these roadblocks firsthand in security operations of all sizes.
Delayed detection and response times
Most standard Indicators of Compromise detection systems react to threats instead of preventing them. So security teams often find threats hours or days after the original compromise. This delay between infection and detection gives attackers the chance to dig in, move through networks, and steal sensitive data. Teams face multiple approval stages that stretch out fix times even after they spot a threat.
Manual triage of alerts leading to slow containment
Security analysts handle Indicators of Compromise alerts mostly by hand, which creates bottlenecks during critical responses. Each alert needs individual checking, verification, and escalation. These tasks eat up valuable time while threats keep spreading. Even successful detection doesn’t solve the containment problem because of manual processes.
Fidelis Deception can speed up detection by identifying attackers during reconnaissance—often before any actual compromise occurs. This enables preemptive containment.
Discover how deception technology helps you:
-
Use decoys to expose hidden threats -
Monitor attacker behavior in real-time -
Shift from reactive to proactive defense
Siloed tools and fragmented visibility
Organizations use separate security tools that can’t talk to each other properly. This split creates dangerous blind spots where threats slip through unnoticed. To cite an instance, network monitoring might catch suspicious traffic without seeing what’s happening on endpoints. This makes a detailed threat analysis almost impossible. Security teams can’t piece together the whole attack story from scattered data points.
Alert fatigue from false positives
The biggest problem might be the flood of false positive alerts from traditional IOC security systems. Security analysts wade through hundreds—maybe even thousands—of daily security alerts. Many come from harmless activities or normal business operations. This constant noise makes teams numb to real threats and wastes resources. Alert fatigue becomes another reason for missed detections and slow responses to Real-Time IOC Detection and Response efforts.
Key Strategies for Real-Time IOC Detection and Threat Containment
.elementor-widget-image{text-align:center}.elementor-widget-image a{display:inline-block}.elementor-widget-image a img[src$=”.svg”]{width:48px}.elementor-widget-image img{vertical-align:middle;display:inline-block}
Security teams need strategic approaches that combine technology and process to detect and respond to Indicators of Compromises effectively. Multiple integrated strategies help identify and contain threats faster when teams want to reduce dwell time.
Automated Cyber Threat Intelligence Integration
Threat containment starts with smooth automation of threat intelligence feeds. Organizations get critical advantages in detection speed when they automatically ingest and normalize indicators of compromise from multiple sources. Security teams can match current activities against known threat patterns and flag potential matches for investigation or automated response.
Endpoint and Network Telemetry Integration
Network security data alone doesn’t provide enough visibility for modern threats. A combination of endpoint and network telemetry creates a complete picture of potential compromise. Endpoint telemetry shows process injections, PowerShell abuse, and other fileless malware techniques that network monitoring might miss. Network telemetry captures communication patterns that endpoint detection might overlook. These data sources help security teams identify suspicious activity earlier in the cyber kill chain. This integrated telemetry approach provides the context to distinguish genuine threats from benign activities.
While automation and telemetry are key pillars, Fidelis Deception can add another critical layer to real-time IOC detection.
Automated Response and Containment Playbooks
Swift containment prevents lateral movement and limits damage after threat detection. Automated response playbooks change this process from hours to minutes by executing predefined actions without manual intervention. Effective playbooks typically include:
- Isolation of affected systems from critical networks
- Blocking of malicious IP addresses and unusual domains
- Revocation of compromised credentials
- Collection of forensic evidence for investigation
These simplified processes balance speed with appropriate human oversight to ensure containment actions match threat severity. Well-designed playbooks help security teams respond to threats at machine speed while you retain control over containment decisions.
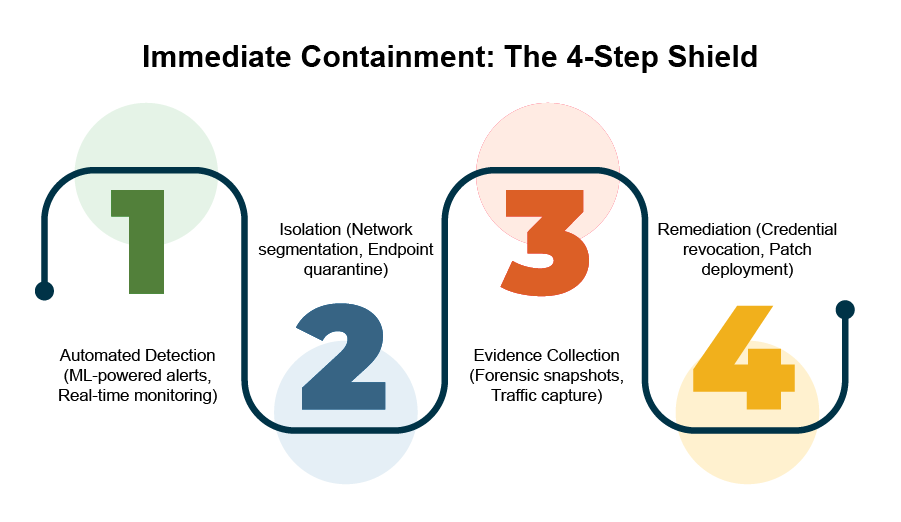
Immediate Containment Strategies
Organizations just need strategic approaches to contain threats without disrupting business operations. Security teams must set up response frameworks that balance quick action with accuracy during incidents.
Building your IOC detection team structure
A well-defined team structure with specialized roles makes indicators of compromise (IOC) detection work better. A tiered analyst system works best—Tier 1 handles monitoring, Tier 2 takes care of investigations, and Tier 3 focuses on advanced threat hunting. This setup will give a clear path for issues to move up the chain while making the best use of everyone’s skills. Fidelis Security suggests central management combined with spread-out response teams to support operations worldwide.
ML-based Alert Prioritization
Alert fatigue remains the biggest problem for security teams. Machine learning algorithms help by finding patterns in past alert data to cut down false alarms. The system can rank alerts by how serious they are, how much they affect business, and which assets they target. This lets analysts focus on real threats. Fidelis Elevate® XDR uses smart ML algorithms to cut through the noise and spot genuine security issues.
Network segmentation as a first response
Network segmentation stops threat actors from moving sideways through your systems right away. Networks with proper segments keep threats from moving past where they first got in. This method keeps data breaches or security events stuck in specific areas. Teams can respond faster because they can see exactly which zones are affected.
Endpoint isolation protocols
Quick endpoint isolation becomes vital once a system shows signs of compromise. Smart isolation protocols can cut off infected devices but still let you watch what’s happening. Fidelis Elevate® lets teams isolate Windows systems selectively, so they can contain threats while keeping business running.
Designing automated containment workflows
Good containment needs tested response playbooks that spell everything out beforehand. These automated systems should list exact steps to isolate, collect evidence, and fix issues. Response times get much longer without these systems, which means more damage can happen.
Balancing automated vs. human-driven response
Human judgment matters just as much as automation. Automated systems handle routine threats while security teams tackle complex cases. This mix utilizes technology’s speed but keeps human insight available for tricky situations that need context to understand properly.
How Fidelis Extended Detection and Response can Help
Deep visibility across endpoint, network, cloud, and deception layers
Fidelis Elevate® gives you unmatched visibility by analyzing telemetry from endpoints, networks, cloud environments, and deception technologies at once. This multi-layered viewpoint monitors every attack vector, whatever their origin.
The platform relates seemingly unconnected indicators of compromise throughout your digital world. These indicators map to the MITRE ATT&CK® framework and provide useful context. This connection is a great way to get insights when threat actors try to hide their suspicious activities across multiple systems—a tactic that usually defeats siloed security tools.
Automated incident response via Fidelis Endpoint Detection and Response
Quick threat containment needs automation, which Fidelis Elevate® delivers through its built-in components. Fidelis Endpoint® watches system for suspicious activities and isolates compromised systems before threats spread. Fidelis Network® examines packets deeply to spot command-and-control communications and data theft attempts up-to-the-minute.
These components enable complete automated responses:
- Immediate endpoint isolation without losing visibility
- Automatic blocking of malicious network connections
- Evidence collection for both immediate response and future digital forensic data analysis
Integration with threat intel feeds and deception technologies
Fidelis Elevate® enhances indicators of compromise (IOC) detection by merging with external threat intelligence sources. This feature keeps your defense mechanisms ready against new threats.
The platform uses deception technologies to place convincing decoys throughout your environment. These decoys act as early-warning tripwires. They alert security teams to attacker presence and reveal their tactics, techniques, and procedures. This information becomes valuable intelligence that strengthens your overall security posture.
Conclusion
Immediate IOC detection serves as a vital shield against modern cyber threats. Our team at Fidelis Security knows that successful threat containment needs smooth integration of automated threat detection, quick response capabilities, and complete visibility in all security layers.
Fidelis Elevate® XDR tackles common Indicators of Compromise detection issues by bringing together endpoint, network, and cloud security. The platform’s automated response features cut down containment times while you retain control of human oversight. ML-based alert prioritization helps security teams using Fidelis Elevate® focus on real cyber threats instead of false positives.
Security teams looking to boost their IOC detection and response should remember these points:
- Automated threat intelligence integration speeds up threat detection
- Endpoint and network telemetry working together gives complete visibility
- Ready-to-use response playbooks allow quick containment
- The right mix of automation and human oversight leads to better response
- Unified threat detection
- Real-time response
- Built-in deception
The post IOC Detection and Response: Strategies for Immediate Threat Containment appeared first on Fidelis Security.