How safe and secure is your iPhone really?
Your iPhone isn’t necessarily as invulnerable to security threats as you may think. Here are the key dangers to watch out for and how to harden your device against bad actors.
28 Apr 2025
•
,
6 min. read

Chances are high that many people think, “it’s an iPhone, so I’m safe”. Apple’s control over its device and app ecosystem has indeed historically been tight, with its walled-garden approach providing fewer opportunities for hackers to find weak spots. There are also various built-in security features like strong encryption and containerization, the latter helping prevent data leakage and limit the spread of malware. And passkey-based logins and various privacy-by-default settings also help.
One of the biggest security advantages of the iOS ecosystem has been the fact that apps are typically sourced from the official Apple App Store and must pass various stringent tests to be approved for listing. This largely curbs the risk of malicious, risky and insecure apps. But this doesn’t eliminate the risks completely. Also, all manner of everyday scams and other threats bombard not just Android, but also iOS users. Some are more common than others, but all demand attention.
Muddying the waters further, given the EU’s anti-monopoly law known as the Digital Markets Act (DMA), Apple must allow:
- Developers to offer iOS apps to users via non-App Store marketplaces. This could increase the chances of users downloading malicious apps. Even legitimate apps may not be updated as frequently as official App Store ones.
- Third-party browser engines, which may offer new opportunities for attack that Apple’s WebKit engine doesn’t (check).
- Third-party device manufacturers and app developers to access various iOS connectivity features, like peer-to-peer Wi-Fi connectivity and device pairing. The tech giant argues this means it may be forced to send sensitive user data including notifications containing personal messages, Wi-Fi network details or one-time codes, to these developers. They could theoretically use the information to track users, it warns.
Where else iOS threats are lurking
While the above may “only” impact EU citizens, there are also other and possibly more immediate concerns for iOS users worldwide. These include:
Jailbroken devices
If you deliberately unlock your device to allow what Apple calls “unauthorized modifications”, it might violate your Software License Agreement and could disable some built-in security features like include Secure Boot and Data Execution Prevention. It will also mean your device no longer receives automatic updates. And by being able to download apps from beyond the App Store, you will be exposed to malicious and/or buggy software.
Malicious apps
While Apple does a good job of vetting apps, it doesn’t get it right 100% of the time. Malicious apps detected on the App Store recently include:
Website-based app downloads
You also need to beware of downloading iOS apps direct from websites with supported browsers. As detailed in ESET’s latest Threat Report, Progressive Web Apps (PWAs) allow direct installation without requiring users to grant explicit permissions, meaning downloads could fly under the radar. ESET discovered this technique used to disguise banking malware as legitimate mobile banking apps.
Phishing/social engineering
Phishing attacks via email, text (or iMessage) and even voice are a common occurrence. They impersonate legitimate brands and trick you into handing over credentials or clicking on malicious links/opening attachments to trigger malware downloads. Apple IDs are among the most highly prized logins as they can provide access to all the data stored in your iCloud account and/or enable attackers to make iTunes/App Store purchases. Look out for:
- Fake pop-ups that claim your device has a security problem
- Scam phone calls and FaceTime calls impersonating Apple Support or partner organizations
- Fake promotions offering giveaways and prize draws
- Calendar invite spam containing phishing links
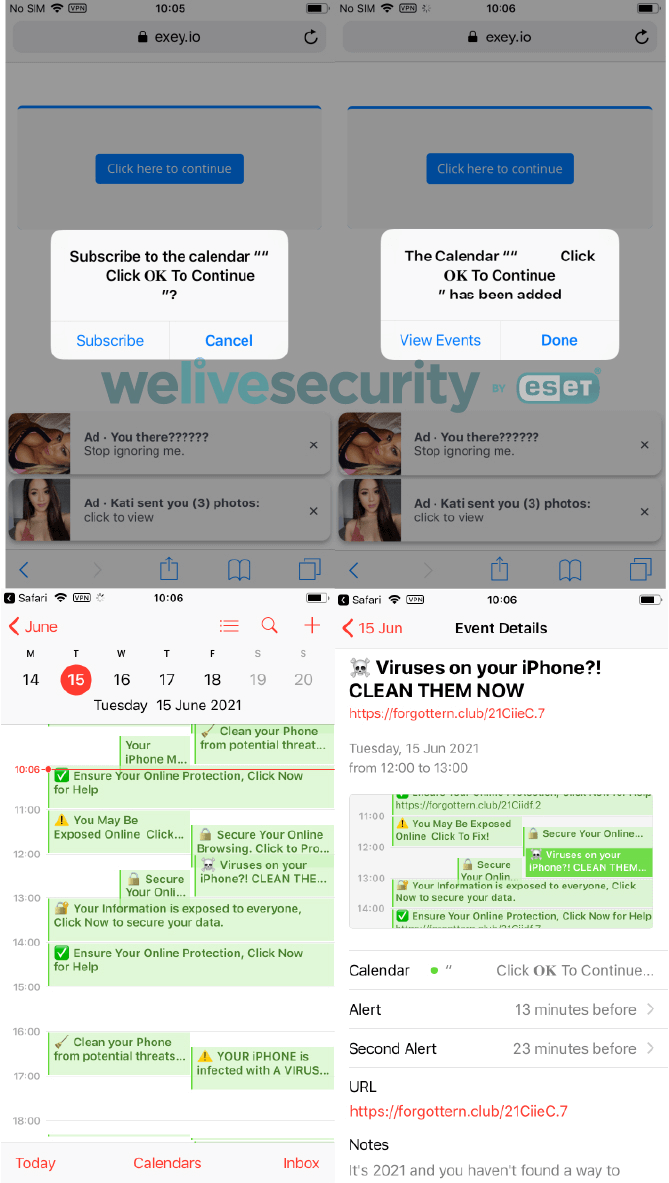
In one highly sophisticated campaign, threat actors used social engineering techniques to trick users into downloading a mobile device management (MDM) profile, giving them control over victims’ devices. With this, they deployed GoldPickaxe malware designed to harvest facial biometric data and use it to bypass banking logins.
Public Wi-Fi risks
If you connect your iPhone to a public Wi-Fi hotspot, beware. It may be a fake lookalike hotspot set up by threat actors designed to monitor web traffic, and steal sensitive information you enter like banking passwords. Even if the hotspot is legitimate, many don’t encrypt data in transit, meaning that hackers with the right tools could view the websites you visit and the credentials you enter.
Here is where a VPN comes in handy, creating an encrypted tunnel between your device and the internet.
Take ESET’s iOS security checklist to learn just how safe your iPhone is.
Vulnerability exploits
Although Apple devotes much time and effort to ensuring its code is free from vulnerabilities, bugs can sometimes creep into production. When they do, hackers can pounce if users haven’t updated their device in time, for example, by sending malicious links in messages that trigger an exploit if clicked on.
- Last year, Apple was forced to patch a vulnerability which could allow threat actors to steal information from a locked device via Siri voice commands
- Sometimes threat actors and commercial companies themselves research new (zero day) vulnerabilities to exploit. Although rare and highly targeted, attacks leveraging these are often used to covertly install spyware to eavesdrop on victim’s devices
Staying safe from iOS threats
This might seem like there’s malware lurking around every corner for iOS users. That might be true, up to a point, but there’s also plenty of things to minimize your exposure to threats. Here are a few of the main tactics:
- Keep your iOS and all apps up to date. This will reduce the window of opportunity for threat actors to exploit any vulnerabilities in old versions to achieve their goals.
- Always use strong, unique passwords for all accounts, perhaps using ESET’s password manager for iOS, and switch on multi-factor authentication if offered. This is easy on iPhones as it will require a simple Face ID scan. This will ensure that, even if the bad guys get hold of your passwords, they won’t be able to access your apps without your face.
- Enable Face ID or Touch ID to access your device, backed up with a strong passcode. This will keep the iPhone safe in the event of loss or theft.
- Don’t jailbreak your device, for the reasons listed above. It will most likely make your iPhone less secure.
- Be phishing-aware. That means treating unsolicited calls, texts, emails and social media messages with extreme caution. Don’t click on links or open attachments. If you really need to do so, check with the sender separately that the message is legitimate (i.e., not by responding to details listed in the message). Look for tell-tale signs of social engineering including:
- Grammatical and spelling errors
- Urgency to act
- Special offers, giveaways and too-good-to-be-true deals
- Sender domains that don’t match the supposed sender
- Avoid public Wi-Fi. If you have to use it, try to do so with a VPN. At the very least, don’t log in to any valuable accounts or enter sensitive information while on public Wi-Fi.
- Try to stick to the App Store for any downloads, in order to minimize the risk of downloading something malicious or risky.
- If you believe you may be a target of spyware (often used by oppressive governments and regimes on journalists, activists and dissidents), enable Lockdown Mode.
- Keep an eye out for the tell-tale signs of malware infection, which could include:
- Slow performance
- Unwanted ad pop-ups
- Overheating
- Frequent device/app crashes
- New apps appearing on the home screen
- Increased data usage
Apple’s iPhone remains among the most secure devices out there. But they’re not a silver bullet for all threats. Stay alert. And stay safe.
