Step-by-Step Guide to Real Threat Detection — Powered by Fidelis Security
.elementor-widget-text-editor.elementor-drop-cap-view-stacked .elementor-drop-cap{background-color:#69727d;color:#fff}.elementor-widget-text-editor.elementor-drop-cap-view-framed .elementor-drop-cap{color:#69727d;border:3px solid;background-color:transparent}.elementor-widget-text-editor:not(.elementor-drop-cap-view-default) .elementor-drop-cap{margin-top:8px}.elementor-widget-text-editor:not(.elementor-drop-cap-view-default) .elementor-drop-cap-letter{width:1em;height:1em}.elementor-widget-text-editor .elementor-drop-cap{float:left;text-align:center;line-height:1;font-size:50px}.elementor-widget-text-editor .elementor-drop-cap-letter{display:inline-block}
In today’s threat landscape, the question is no longer “Will we be attacked?” but “How fast can we detect and respond when it happens?” The unfortunate reality is that many organizations struggle to detect threats in time—often because their tools operate in silos, their teams are overloaded with false positives, and they lack the necessary context to act swiftly and accurately.
This is where a unified, intelligence-driven detection strategy becomes critical. In this guide, we’ll walk through the key building blocks of real-world threat detection—and how each one, if not handled properly, can open dangerous gaps. For each step, you’ll also see how Fidelis Security, through its integrated platform, helps close those gaps and empower security teams to stay ahead of threats.
.elementor-heading-title{padding:0;margin:0;line-height:1}.elementor-widget-heading .elementor-heading-title[class*=elementor-size-]>a{color:inherit;font-size:inherit;line-height:inherit}.elementor-widget-heading .elementor-heading-title.elementor-size-small{font-size:15px}.elementor-widget-heading .elementor-heading-title.elementor-size-medium{font-size:19px}.elementor-widget-heading .elementor-heading-title.elementor-size-large{font-size:29px}.elementor-widget-heading .elementor-heading-title.elementor-size-xl{font-size:39px}.elementor-widget-heading .elementor-heading-title.elementor-size-xxl{font-size:59px}
Why Threat Detection Fails Without Unified Visibility—And How Fidelis Fixes It
.elementor-widget-image{text-align:center}.elementor-widget-image a{display:inline-block}.elementor-widget-image a img[src$=”.svg”]{width:48px}.elementor-widget-image img{vertical-align:middle;display:inline-block}
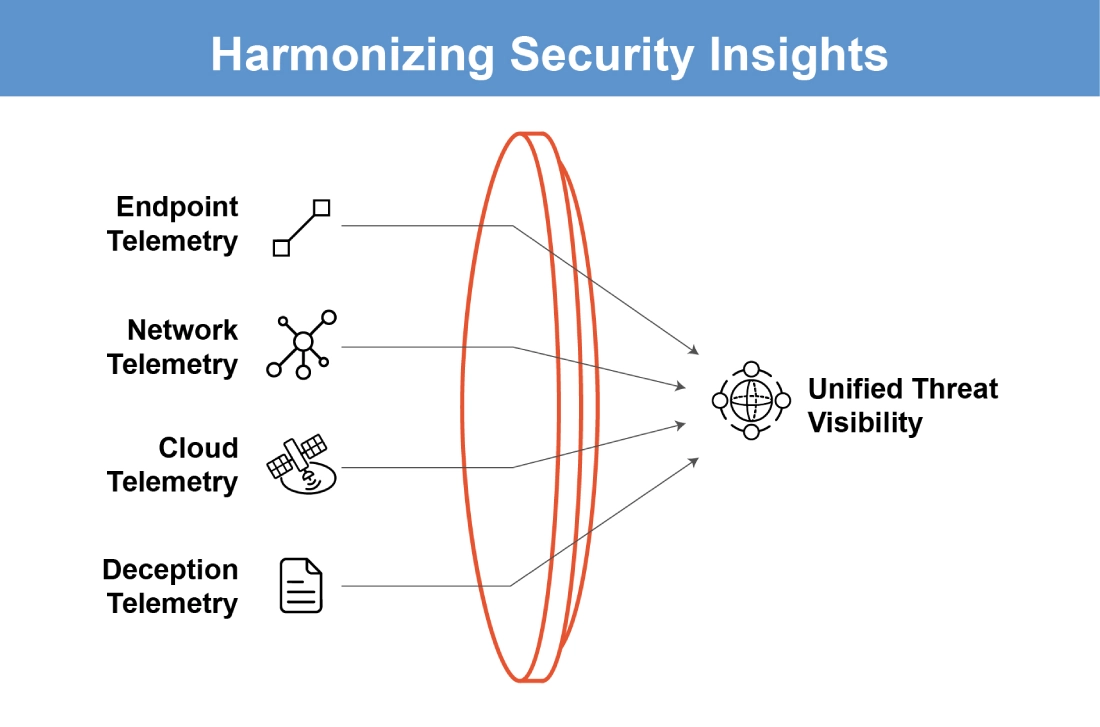
You can’t defend what you can’t see. When organizations use a mix of disconnected tools—one for endpoint, another for network, another for cloud—the result is a fragmented view of their threat landscape. This not only increases the chance of missing coordinated attacks but also slows down investigation and response due to a lack of shared context.
Fidelis Elevate solves this by unifying telemetry from endpoint, network, cloud, and deception layers into one correlated platform. Instead of switching between tools and piecing together fragmented data, analysts get a full-spectrum, contextualized view of threats—ready to act on.
How to Detect Real Threats: A Practical Roadmap
1. Start with Deep Network Detection
Real-time threat detection starts with understanding your network—especially east-west traffic, which is often where lateral movement and data exfiltration occur post-breach. If you’re only monitoring north-south traffic or relying on metadata-level analysis, attackers can move undetected inside your infrastructure.
Fidelis Network dives deep into the traffic flowing through your environment. It analyzes encrypted and unencrypted packets in real time using:
-
Deep Packet Inspection (DPI): Granular payload visibility -
Encrypted Traffic Analysis (ETA): Identifies threats hiding in TLS/SSL flows -
Lateral Movement Detection: Detects unauthorized internal movement -
Threat Intel Integration: Correlates traffic patterns with known IOCs
Instead of just detecting anomalies, Fidelis contextualizes them—mapping activity to behaviors and known attack frameworks
2. Layer in Endpoint Detection for Full Coverage
Even with strong perimeter and network defenses, endpoints remain a frequent point of compromise. Without continuous endpoint visibility, attackers can escalate privileges, install backdoors, and carry out persistence techniques—completely undetected.
Fidelis Endpoint ensures that endpoint activity is never a blind spot. It delivers:
-
Real-Time Behavioral Monitoring: Tracks suspicious process and file activity -
Historical Forensics: Replays attack timelines for full understanding -
Root Cause Analysis: Pinpoints how threats entered and what they affected -
On-Demand Response: Isolate hosts, kill processes, and collect snapshots
Because it’s tightly integrated with network telemetry, alerts are enriched and correlated—reducing noise and duplication across tools.
3. Catch Advanced Threats: Lure, Trap, Analyze
Sophisticated attackers often bypass traditional defenses by appearing legitimate. If your detection relies solely on known signatures or static policies, you’re reacting to what’s already known—not proactively identifying unknown threats.
Deception changes that. Fidelis Deception lets you take the offensive by deploying fake assets throughout your environment. These include:
-
Fake credentials that detect brute-force attempts -
Decoy file shares and servers to expose intruders -
Breadcrumbs and traps that reveal lateral movement
Since legitimate users never interact with deception assets, any engagement is a clear sign of malicious intent—giving you early, low-noise alerts that matter.
4. Use Fidelis XDR to Correlate Threats Across Every Vector Automatically
Threat actors don’t operate in one layer—they pivot across endpoints, networks, and user credentials. If your detection lacks automated correlation, you’ll either miss the bigger picture or waste time manually connecting the dots.
Fidelis XDR does this correlation for you. It brings together alerts and telemetry from across your stack to create:
-
Unified Threat Timelines: Tracks the full progression of an attack -
Multi-Vector Case Creation: Groups related alerts into one case -
MITRE ATT&CK Mapping: Maps behaviors to tactics and techniques -
One-Click Investigation: Lets analysts zoom in on each stage instantly
You’re not just reacting to isolated alerts—you’re responding to full attack stories as they unfold.
5. Prioritize Threats Using ML Threat Scoring and Visual Timelines
When everything looks urgent, nothing is. Alert fatigue happens when all alerts are treated equally—forcing analysts to sift through thousands of notifications just to find the real threats.
Fidelis Elevate helps security teams cut through the noise with:
-
ML-Driven Threat Scoring: Assigns risk levels based on severity, asset value, and impact -
Graphical Attack Timelines: Visual maps that show attacker activity, escalation, and spread -
Critical Path Highlighting: Shows where the attacker is in the kill chain
This clarity reduces triage time dramatically and helps your team focus on what truly matters.
6. Launch a Response in Seconds with Integrated Playbooks and Containment
A fast, precise response is essential in limiting damage—but it’s often delayed because analysts must pivot between tools or rely on manual processes. Without integrated response capabilities, detection becomes a dead-end.
Fidelis Elevate makes response seamless. You can:
-
Isolate endpoints immediately upon detection -
Block malicious domains or IPs at the perimeter -
Kill processes that are behaving suspiciously -
Execute playbooks tailored for threats like ransomware or phishing
All actions are executed within the same platform—ensuring swift and coordinated response without losing context.
7. Threat Hunting That Goes Beyond Logs and Alerts
Waiting for alerts means you’re already behind. Many threats remain dormant or undetected because they don’t match known signatures. Proactive threat hunting is the only way to find them—but it requires rich data and the ability to ask complex questions of your environment.
Fidelis Threat Hunting enables analysts to:
-
Query full-packet captures and endpoint telemetry -
Use threat intel overlays to hunt for emerging IOCs -
Run prebuilt or custom hunt queries based on known TTPs -
Access historical data for retrospective analysis
This turns your SOC into a proactive force—finding stealthy threats before they escalate into incidents.
Discover how XDR is changing the game for organizations looking to:
-
Close security gaps with a unified solution -
Automate threat detection and response for faster actions -
Simplify security management across all environments
Why Security Teams Choose Fidelis Over Patchwork Solutions
Most security teams juggle multiple tools that weren’t built to work together. The result is alert fatigue, missed threats, and slow responses. By contrast, Fidelis offers a unified solution that delivers:
-
Seamless visibility across every attack surface -
Intelligent correlation of signals from multiple vectors -
Integrated deception to trap advanced threats -
Built-in response actions without context-switching -
A single UI for all detection, investigation, and response tasks
Final Thoughts: Ready for Real Threat Detection?
Today’s attackers are fast, stealthy, and relentless. Defending against them requires more than patchwork tools and reactive playbooks. You need an integrated approach that offers full visibility, intelligent correlation, proactive detection, and instant response.
That’s what Fidelis delivers—without the noise, without the blind spots, and without the delays.
If your goal is to stay ahead of threats—not just survive them—this is where your detection journey begins.
Frequently Ask Questions
Why is real-time threat detection still a challenge for most organizations?
Most organizations struggle with fragmented security tools that operate in silos—each monitoring a different part of the environment. This leads to blind spots, delayed responses, and a lack of unified context, making real-time detection nearly impossible. Without integrated visibility and intelligent correlation, threats often go unnoticed until damage is done.
How does Fidelis Elevate differ from traditional SIEM or EDR solutions?
Unlike traditional SIEMs or standalone EDRs that only focus on logs or endpoints, Fidelis Elevate combines network, endpoint, cloud, and deception data into a unified detection and response platform. It automates correlation across these layers, giving security teams a complete, contextual view of threats—without manual stitching of data.
Is deception technology really effective in modern threat detection?
Yes. Deception adds a proactive layer of defense by luring attackers into interacting with fake assets. These interactions generate high-confidence alerts, as legitimate users don’t touch decoy systems. Fidelis Deception makes this easy to deploy and manage, allowing early detection of lateral movement and insider threats.
The post Step-by-Step Guide to Real Threat Detection — Powered by Fidelis Security appeared first on Fidelis Security.