The 12 Cybersecurity Platforms That Define Modern Security
Hello, Cyber Builders 🖖
We’re continuing our deep dive into cybersecurity platforms. This is the third post in the series. If you missed the first two, links are provided at the bottom of this article.
This week, I asked myself a simple but crucial question: What is a cybersecurity platform? I’m not talking about vendors or branding. What features should be bundled together in a way that makes sense?
It’s easy to slap everything into one big cloud-based application, but that doesn’t automatically make it a coherent platform. So, in this post, we’ll explore why coherence matters and take a look at how Gartner categorizes platforms (trust me, it’s entertaining). Finally, I’ll share my list of 12 strong cybersecurity platform candidates.
-
I explain why a single, do-it-all security platform will never exist and why cybersecurity will always have general-purpose and specialized solutions.
-
I take a lighthearted but critical look at Gartner’s ever-growing acronym Jungle and what their take on security platform convergence means.
-
I share 12 cybersecurity platform categories that define how organizations can structure their security stacks today.
-
Finally, I discuss why AI is about to disrupt everything, breaking down traditional security silos and reshaping the industry.
Many sales teams dream of having one big platform that does everything. Honestly, 20 years ago, people thought it was possible. Back then, security was seen as a point issue. Solve it once, and boom—everyone would be securely connected to the Internet.
Fast-forward two decades and reality has proven otherwise. Threats have evolved, and security challenges have moved from local networks to data centers to cloud applications and mobile devices. Remote work has completely shifted the paradigm, and AI is about to reshuffle the cards.
But here’s the real issue: it’s not just about features or infrastructure. It’s about taste and user empathy.
In any market, you always have two types of products (and a broad spectrum in the middle):
-
General-purpose platforms – broad, easy-to-use solutions for those who want “just enough” security at the right price.
-
Specialized tools – cutting-edge technology for experts who demand the latest features and highest protection.
Cybersecurity is no different. Customers will always seek simplicity; others will chase the most advanced solutions. That’s why a single “do-it-all” platform will never fully replace niche security products.
It’s all about positioning. Who’s your customer? What are their pains? What’s their environment? What language do they speak—both literally and technically? Whether you’re designing a cybersecurity platform or selling cornflakes, these product and marketing questions remain the same.
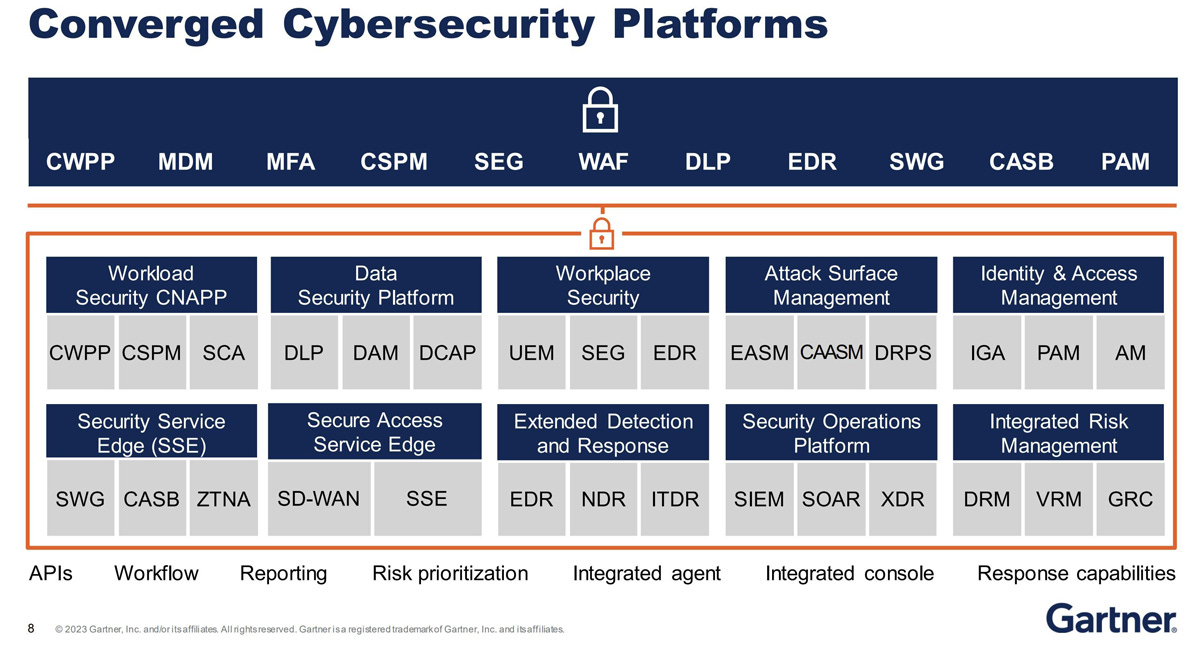
Look at this picture from a Gartner blog post about convergence in the product and platform space.
First of all, it’s pretty funny—if there’s one thing I’ve realized since starting Cyber Builders, it’s that the vocabulary in cybersecurity is absurdly complex. Why do we keep inventing all these acronyms?
Anyone walking the halls of RSA in San Francisco or FIC in Lille will see a flood of acronyms. Are you an EDR or a CSPM? Is that something you say or talk to? Of course not. Cybersecurity terminology needs to be more natural and intuitive. Instead, we have an ever-increasing soup of abbreviations that makes navigating the field harder.
That’s why Gartner’s perspective on platforms is interesting—especially in the context of a) what I just said about who the customer is, who the user is, and what the actual goal of a platform should be but b) that Gartner himself is a source of acronyms!
Still, their take on convergence highlights how security platforms are positioned and how the industry tends to overcomplicate things.
Buckle up!
-
Secure Web Gateways (SWG), CASB, and Zero Trust Network Access (ZTNA) are merging to become security service edge (SSE)
-
But SSE + SD-WAN = SASE (secure access service edge)
-
EDR, NDR, and Identity Threat and Detection Response (ITDR) are merging into XDR platforms
-
But now, XDR has joined SIEM (and next-gen SIEM) and SOAR to become a Security Operations Platform (aka SecOps Platform)
-
In cloud security, cloud workload protection platforms (CWPP) became cloud security posture management (CSPM)
-
But CSPM+ Software Composition Analysis (SCA) = CNAPP platforms.
And there is more!
-
Data Security: Includes DLP, digital asset management, and data-centric audit and protection (DCAP)
-
Workplace Security: Combines UEM, secure email gateways, and EDR
-
Attack Surface Management: external & cyber asset ASM (EASM and CAASM) and digital risk protection services (DRPS)
-
Identity and Access Management: Includes access management (IAM), PAM and identity governance and administration (IGA)
-
Integrated Risk Management: Digital rights management (DRM), vendor risk management (VRM), and GRC
Now, let’s get to the actual substance—what I see as the 12 key cybersecurity platform categories. These aren’t vendor-specific but rather coherent feature sets that define what a trustworthy security platform should offer.
These are my current take. I am happy to get feedback, comments, and direct messages to challenge it and publish a community-validated post later in the year.
-
Network Security – Protects networks and data flows from unauthorized access and misuse. Shields users from web-based threats.
🔹 Firewalls, IDS/IPS, SASE, ZTNA, VPNs, network segmentation, traffic analysis, SWGs.
-
Endpoint Security – Secures endpoint devices (PCs, Macs, mobile) from cyber threats.
🔹 Antivirus, EDR, MDM, device encryption, application whitelisting, patch management.
-
Cloud Security – Protects cloud environments, workloads, and applications.
🔹 Cloud workload protection, container security, configuration management, vulnerability scanning.
-
Continuous Threat Exposure Management (CTEM) – Identifies and validates exposures, reducing false positives.
🔹 Automated vulnerability scanning, attack surface management, penetration testing, and exposure triage.
-
User Awareness & Training – Equips users with the knowledge to act as a defense layer.
🔹 Phishing simulations, interactive training, secure behavior analytics.
-
GRC & Compliance – Manages governance, risk, and compliance obligations.
🔹 Compliance tracking, policy management, regulatory alignment, supply chain security.
-
Identity & Access Management (IAM) – Secures digital identities and controls access.
🔹 SSO, MFA, PAM, identity analytics, API security.
-
SOC Enablement Technologies – Powers the Security Operations Center with advanced detection and response tools.
🔹 SIEM, TIP, deception technology, high-fidelity alerting.
-
Application Security (AppSec) – Identifies and mitigates application vulnerabilities.
🔹 SAST, DAST, IAST, RASP, API security.
-
Data Security – Protects sensitive data from unauthorized access and loss.
🔹 Data encryption, access control, content filtering, data masking.
-
Fraud Detection & Transaction Security – Prevents fraudulent transactions and insider threats.
🔹 Transaction monitoring, behavioral analysis, anomaly detection, fraud scoring.
-
Resilience Platform – Ensures business continuity through preparation, recovery, and adaptation.
🔹 Backups, IT infrastructure mapping, critical system assessment, tabletop exercises.
These are the significant pillars I see when looking at cybersecurity platforms. Whether you’re aiming for a broad or specialized solution, it all comes down to who your customers are and what problem they need to solve.
One thing is sure—this landscape isn’t static. AI is about to reshuffle everything.
For years, cybersecurity has been built around distinct categories and specialized tools. Each domain—network, endpoint, and cloud security—has dedicated solutions, policies, and teams. These silos exist because, historically, no single technology could handle all aspects of security at once. The complexity of threats and the diversity of IT environments made breaking security into manageable components necessary.
But that’s changing. AI-driven security agents are poised to disrupt this entire model. Instead of having separate products for every function, AI will enable continuous, adaptive, and context-aware security across all domains.
Of course, this shift won’t happen overnight, and it will bring its challenges. But one thing is clear: AI is set to redefine how we think about security platforms.
And that’s a topic for another post. Stay tuned—because the AI-driven security revolution is just beginning. 🚀
Laurent 💚